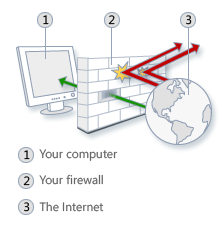
SECURITY THREATS
In computer security a threat is a possible danger that might exploit a vulnerability to breach security and therefore cause possible harm.
In computer security a threat is a possible danger that might exploit a vulnerability to breach security and therefore cause possible harm. A threat can be either "intentional" (i.e. hacking: an individual cracker or a criminal organization) or "accidental" (e.g. the possibility of a computer malfunctioning, or the possibility of a natural disaster such as an earthquake, a fire, or a tornado) or otherwise a circumstance, capability, action, or event.
A potential cause of an incident, that may result in harm of systems and organization
Computer security threats are relentlessly inventive. Masters of disguise and manipulation, these threats constantly evolve to find new ways to annoy, steal and harm. Arm yourself with information and resources to safeguard against complex and growing computer security threats and stay safe online.
Computer Virus Threats
A computer virus is a program or piece of code that is loaded onto your computer without your knowledge and runs against your wishes. Viruses can also replicate themselves. All computer viruses are man-made. A simple virus that can make a copy of itself over and over again is relatively easy to produce. Even such a simple virus is dangerous because it will quickly use all available memory and bring the system to a halt. An even more dangerous type of virus is one capable of transmitting itself across networks and bypassing security systems.
Spyware Threats
Spyware is software that is installed on a computing device without the end user's knowledge. Such software is controversial because even though it is sometimes installed for relatively innocuous reasons, it can violate the end user's privacy and has the potential to be abused.
Spyware that is installed for innocuous reasons is sometimes referred to as tracking software. In the workplace, such software may be installed on corporate laptops to monitor employees' browsing activities. In the home, parents might install a keystroke logger to monitor their children's activity on the internet. Or an advertiser might use cookies to track what webpages a user visits in order to target advertising in a contextual marketing campaign. If the end user is told that data is being collected and has the ability to learn with whom the data is being shared, such data collection programs are not considered spyware.
Hackers & Predators
People, not computers, create computer security threats and malware. Hackers and predators are programmers who victimize others for their own gain by breaking into computer systems to steal, change or destroy information as a form of cyber-terrorism. What scams are they using lately? Learn how to combat dangerous malware and stay safe online.
Phishing Threats
Masquerading as a trustworthy person or business, phishers attempt to steal sensitive financial or personal information through fraudulent email or instant messages. How can you tell the difference between a legitimate message and a phishing scam? Educate yourself on the latest tricks and scams.
Phishing is a form of fraud in which the attacker tries to learn information such as login credentials or account information by masquerading as a reputable entity or person in email, IM or other communication channels.
Phishing is the attempt to obtain sensitive information such as usernames, passwords, and credit card details (and sometimes, indirectly, money), often for malicious reasons, by masquerading as a trustworthy entity in an electronic communication.
computer worm
A computer worm is a standalone malware computer program that replicates itself in order to spread to other computers. Often, it uses a computer network to spread itself, relying on security failures on the target computer to access it. Unlike a computer virus, it does not need to attach itself to an existing program.
Trojan horse
In computing, Trojan horse, or Trojan, is any malicious computer program which is used to hack into a computer by misleading users of its true intent. The term is derived from the Ancient Greek story of the wooden horse that was used to help Greek troops invade the city of Troy by stealth.
A destructive program that masquerades as a benign application. Unlike viruses, Trojan horses do not replicate themselves but they can be just as destructive. One of the most insidious types of Trojan horse is a program that claims to rid your computer of viruses but instead introduces viruses onto your computer. The term comes from the a Greek story of the Trojan War, in which the Greeks give a giant wooden horse to their foes, the Trojans, ostensibly as a peace offering. But after the Trojans drag the horse inside their city walls, Greek soldiers sneak out of the horse's hollow belly and open the city gates, allowing their compatriots to pour in and capture Troy.
computer Bomb
A logic bomb is a piece of code inserted into an operating system or software application that implements a malicious function after a certain amount of time, or specific conditions are met. Logic bombs are often used with viruses, worms, and trojan horses to time them to do maximum damage before being noticed.
Trap door
A computer trapdoor, also known as a back door, provides a secret -- or at least undocumented -- method of gaining access to an application, operating system or online service. Programmers write trapdoors into programs for a variety of reasons. Left in place, trapdoors can facilitate a range of activities from benign troubleshooting to illegal access.
spoofs
A technique used to gain unauthorized access to computers, whereby the intruder sends messages to a computer with an IP address indicating that the message is coming from a trusted host.
the term spoof refers to hacking or deception that imitates another person, software program, hardware device, or computer, with the intentions of bypassing security measures. One of the most commonly known spoofing is IP spoofing
Email viruses
When that file is opened, the virus does its damage. Macro viruses can come in Microsoft Word documents that are sent as e-mail attachments. The macro causes the damage when the document is opened providing macro processing has not been disabled within the Microsoft Word application.
Macro virus
A macro virus is a computer virus that "infects" a Microsoft Word or similar application and causes a sequence of actions to be performed automatically when the application is started or something else triggers it. Macro viruses tend to be surprising but relatively harmless.
An example of a macro virus is the Melissa virus which appeared in March 1999. When a user opens a Microsoft Word document containing the Melissa virus, their computer becomes infected. The virus then sends itself by email to the first 50 people in the person's address book.
Malicious software
Malicious software, commonly known as malware, is any software that brings harm to a computer system. Malware can be in the form of worms, viruses, trojans, spyware, adware and rootkits, etc., which steal protected data, delete documents or add software not approved by a user.
'Malware' is an umbrella term used to refer to a variety of forms of hostile or intrusive software, including computer viruses, worms, trojan horses, ransomware, spyware, adware, scareware, and other malicious programs. It can take the form of executable code, scripts, active content, and other software.
Network and Denial of Services Attack
A denial of service (DoS) attack is an incident in which a user or organization is deprived of the services of a resource they would normally expect to have. In a distributed denial-of-service, large numbers of compromised systems (sometimes called a botnet) attack a single target.
Although a DoS attack does not usually result in the theft of information or other security loss, it can cost the target person or company a great deal of time and money. Typically, the loss of service is the inability of a particular network service, such as e-mail, to be available or the temporary loss of all network connectivity and services. A denial of service attack can also destroy programming and files in affected computer systems. In some cases, DoS attacks have forced Web sites accessed by millions of people to temporarily cease operation.
In computing, a denial-of-service attack (DoS attack) is a cyber-attack where the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to the Internet. Denial of service is typically accomplished by flooding the targeted machine or resource with superfluous requests in an attempt to overload systems and prevent some or all legitimate requests from being fulfilled